Inaccessible websites
The following websites are inacessible on a “normal” basis in China, by that I mean that you expect them to be unavailable due to their social features:
The first problem when using Google as the default search engine is that searching in your browser search bar does not work by default anymore. Switch to Yahoo or any other search engine. The second problem is that a lot of websites link to Google, Facebook or Twitter and when accessing those websites that are not blocked by default, loading the website is very slow. Stackoverflow for example links to Google API jquery).
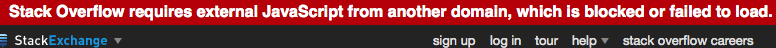
More websites were shut down recently:
- Gmail: since end of 2014, however it still seems to be accessible by IMAP (I do not know about POP) from time to time.
- Lemonde (french news website)
However mails are working between mainland China email services (QQ, sina, …) and Gmail.
DNS Poisoning
China uses lots of DNS poisoning to lure users on other websites: it redirects a user to random (or not?) IP address instead of the correct server. That is the easiest way to block a website.
$ host facebook.com 8.8.8.8 # Using google DNS
Using domain server:
Name: 8.8.8.8
Address: 8.8.8.8#53
Aliases:
facebook.com has address 176.9.157.163
facebook.com has address 205.147.110.246
facebook.com has address 72.29.66.35
$ host facebook.com 211.140.13.188 # Using China DNS
Using domain server:
Name: 211.140.13.188
Address: 211.140.13.188#53
Aliases:
facebook.com has address 164.138.18.241
$ telnet 164.138.18.241 21
Trying 164.138.18.241...
Connected to mail7.rayan.biz
$ host facebook.com 211.140.188.188 # Using China DNS
Using domain server:
Name: 211.140.188.188
Address: 211.140.188.188#53
Aliases:
facebook.com has address 216.243.142.6
$ host 216.243.142.6
6.142.243.216.in-addr.arpa domain name pointer private-c142-d6.arcustech.com.
SSL certificates are then invalid, and a user may input its credential on any website if the website is doing some phishing.
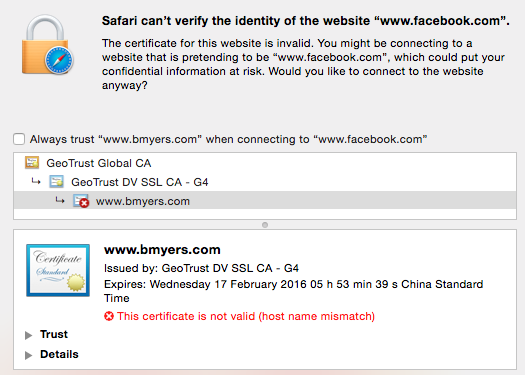
Changing the DNS
China seems to have several layers of blocking, from simple “unresponsive domains” to killing the connection.
A simple way to access to more websites is to simply use an external DNS, for example Google DNS at IP: 8.8.8.8.
However, this won’t stop killing connections.
TCP Reset
Highlighted below are TCP RST packets ([R]) being injected by China to kill the connection to Lemonde. Note the high TTL.
$ sudo tcpdump -v -s 0 'tcp and src host 93.184.220.20'
tcpdump: data link type PKTAP
tcpdump: listening on pktap, link-type PKTAP (Packet Tap), capture size 65535 bytes
03:15:23.732083 IP (tos 0x0, ttl 50, id 0, offset 0, flags [DF], proto TCP (6), length 60)
93.184.220.20.http > 192.168.1.114.54030: Flags [S.], cksum 0x2c39 (correct), seq 1931340408, ack 951517530, win 14480, options [mss 1440,sackOK,TS val 300068050 ecr 210022674,nop,wscale 9], length 0
03:15:36.520874 IP (tos 0x0, ttl 50, id 18266, offset 0, flags [DF], proto TCP (6), length 52)
93.184.220.20.http > 192.168.1.114.54030: Flags [.], cksum 0x55f6 (correct), ack 17, win 29, options [nop,nop,TS val 300071204 ecr 210035232], length 0
03:15:37.544366 IP (tos 0x0, ttl 199, id 55674, offset 0, flags [DF], proto TCP (6), length 40)
93.184.220.20.http > 192.168.1.114.54030: Flags [R.], cksum 0x45bc (correct), seq 1, ack 35, win 772, length 0
03:15:37.545986 IP (tos 0x0, ttl 200, id 55773, offset 0, flags [DF], proto TCP (6), length 40)
93.184.220.20.http > 192.168.1.114.54030: Flags [R.], cksum 0x4007 (correct), seq 1461, ack 35, win 773, length 0
03:15:37.545990 IP (tos 0x0, ttl 201, id 55880, offset 0, flags [DF], proto TCP (6), length 40)
93.184.220.20.http > 192.168.1.114.54030: Flags [R.], cksum 0x349e (correct), seq 4381, ack 35, win 774, length 0
03:15:37.546009 IP (tos 0x0, ttl 64, id 25333, offset 0, flags [none], proto TCP (6), length 40)
93.184.220.20.http > 192.168.1.114.54030: Flags [R], cksum 0x52ba (correct), seq 1931340409, win 12361, length 0
03:15:37.747109 IP (tos 0x0, ttl 50, id 18267, offset 0, flags [DF], proto TCP (6), length 52)
93.184.220.20.http > 192.168.1.114.54030: Flags [.], cksum 0x4efd (correct), ack 35, win 29, options [nop,nop,TS val 300071559 ecr 210036644], length 0
See TCP Reset Attack on Wikipedia for more information.
SSH Proxy
Another way to bypass the Great Firewall is to ssh’s dynamic port forwarding feature if you have an ssh access to a server outside of China. ssh then acts as a SOCKS server, and just change the browser connection to connect to the SOCKS server on localhost.
$ ssh -C -D LOCAL_PORT login@remoteserver # use -C for compression
The problem is that the Great Firewall seems to detect ssh connections and drop packets on the way. This results in high packet loss rate, and the ssh connection needs to be restarted frequently just after a few minutes.
OpenVPN
A VPN is another way to bypass the Great Firewall. I had access to an OpenVPN configuration, however VPN connections are also detected and may be killed.
TCP
It seems that China can detect or/and kill the OpenVPN connection when it is initiated.
Attempting to establish TCP connection with [AF_INET]XXX.XXX.XXX.XXX:YYY [nonblock]
MANAGEMENT: >STATE:TCP_CONNECT,,,
TCP: connect to [AF_INET]XXX.XXX.XXX.XXX:YYY failed, will try again in 5 seconds: Connection reset by peer
MANAGEMENT: >STATE:RESOLVE,,,
MANAGEMENT: >STATE:TCP_CONNECT,,,
TCP: connect to [AF_INET]XXX.XXX.XXX.XXX:YYY failed, will try again in 5 seconds: Connection reset by peer
UDP
As TCP connections are killed via RST packets, using a UDP server and client works well because it is connectionless.
Even if the Great Firewall can detect packets from UDP stream belonging to a VPN and drop some, I found this setup to work best as a VPN.
Shadowsocks
Shadowsocks is a secured SOCKS5 Proxy with several implementations. Because it opens multiple connections and encrypts the traffic, it works better than all the other VPN options available.